Looking for the best hacking software tools? From Sniper to OWASP Nettacker, Kismet to nMap, Nessus and more, there are plenty of ethical hacking software options. But which one is the best? Below, we’ve rounded up a list of the 8 best hacking software tools that you can use on your journey to become an ethical hacker.
Best Hacking Software for Ethical Hackers
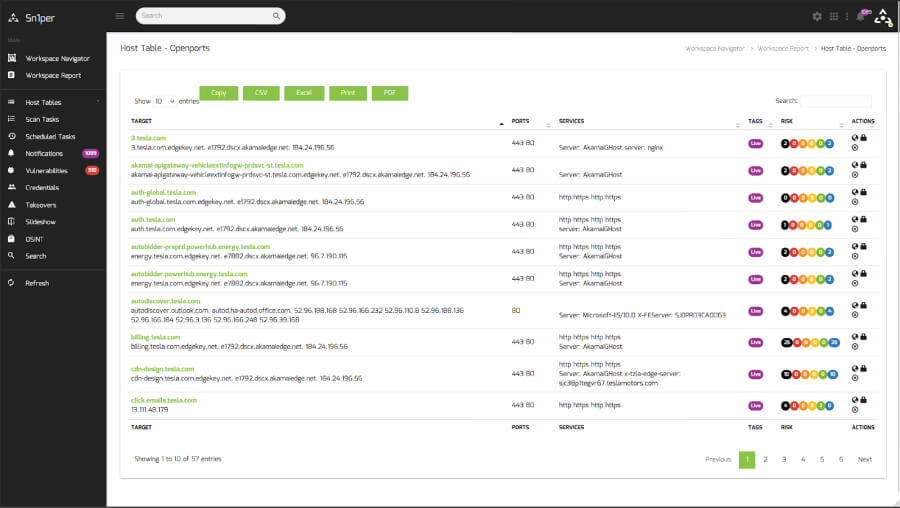
Tool 1: Sn1per
Sn1per is a tool that helps security experts check for vulnerabilities in networks and systems. It automates many routine tasks, making it quicker and easier to identify potential security issues. Sn1per can scan a system to gather preliminary data, identify open ports, and run specific security tests automatically.
Pros:
- Saves Time: Sn1per automates many tasks that would typically take a lot of time if done manually.
- Comprehensive: It can run a variety of security checks, providing a broad view of potential vulnerabilities.
- Customizable: Users can add specific features or tools to fit their particular security testing needs.
- Regular Updates: The tool is regularly updated to handle the latest security threats.
- User-Friendly Interface: The professional version comes with a web interface that simplifies managing and reviewing results.
Cons:
- Complex for Beginners: The range of features and options might be overwhelming for those new to security testing.
- Demands Resources: Running detailed scans and managing large amounts of data can strain computer resources.
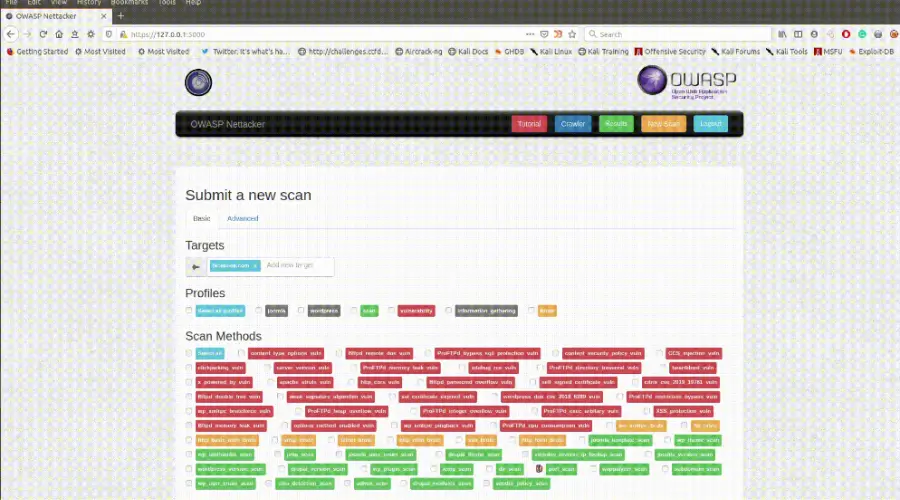
Tool 2: OWASP Nettacker
OWASP Nettacker is an open-source tool designed to help test the security of networks. It automatically scans networks to gather information, check for open ports, and identify potential security weaknesses. It's particularly useful for testing the defences of network systems and is developed by a community of security experts.
Pros:
- Free and Open Source: Anyone can use or modify it without cost, and it benefits from updates and improvements made by a global community.
- Diverse Scanning Capabilities: Capable of performing a wide range of security tests, from simple to complex.
- Efficient: Automates the scanning process, saving time and reducing manual work.
- Community Supported: Regular updates and support from the OWASP community ensure it stays relevant and effective.
Cons:
- Initial Setup: May be tricky to set up and configure, especially for those less familiar with such tools.
- Reliant on Community: The quality and frequency of updates depend on the community, which can vary.

Tool 3: WhatWeb
WhatWeb is a tool designed to scan websites and identify the technologies used on them. It utilises over 1700 plugins to recognize everything from content management systems (CMS) like WordPress to various scripting languages. This allows users to understand the building blocks of any website they are analysing.
Pros:
- Extensive Detection: With over 1700 plugins, WhatWeb can identify a wide range of technologies used on websites, providing comprehensive insights.
- Versatile Use: Useful for security professionals to assess what technologies are in use on a site, which can help in vulnerability assessment.
- Easy to Use: Users can quickly scan websites without needing deep technical knowledge of each technology.
Cons:
- Overwhelming Information: For beginners, the extensive data provided might be difficult to parse and understand fully.
- Dependence on Plugins: The effectiveness of the tool depends on the relevance and updates of its plugins, which can vary in quality.

Tool 4: Grep.app
Grep.app is a search tool that allows users to sift through billions of lines of code across open-source repositories without the need to download or check out the repositories themselves. This is especially useful for developers and security professionals looking to find specific pieces of code or understand code usage across multiple projects.
Pros:
- Broad Reach: Can search through a vast amount of code across numerous repositories, offering wide coverage.
- Convenient: Does not require users to download large amounts of data, making code searches quick and accessible.
Cons:
- Requires Understanding of Code: While it's a powerful tool, users need to have a good understanding of coding to effectively use Grep.app.
- Dependent on External Data: The utility of Grep.app is tied to the availability and quality of code in the repositories it searches.

Tool 5: Nmap
Nmap is a network scanning tool used for mapping networks, scanning for open ports, and detecting running services. It's an essential tool for regular network security checks, helping administrators ensure their networks are secure.
Pros:
- Versatile: Can perform a variety of network scanning tasks, from basic to advanced.
- Widely Used: Trusted by security professionals worldwide for its reliability and effectiveness.
- Open Source: Available for free and supported by a large community of users and developers.
Cons:
- Complex Interface: The wide range of features can make it intimidating for beginners.
- May Raise Security Concerns: Some network administrators might view Nmap scans as potential security threats, leading to unnecessary alarms.
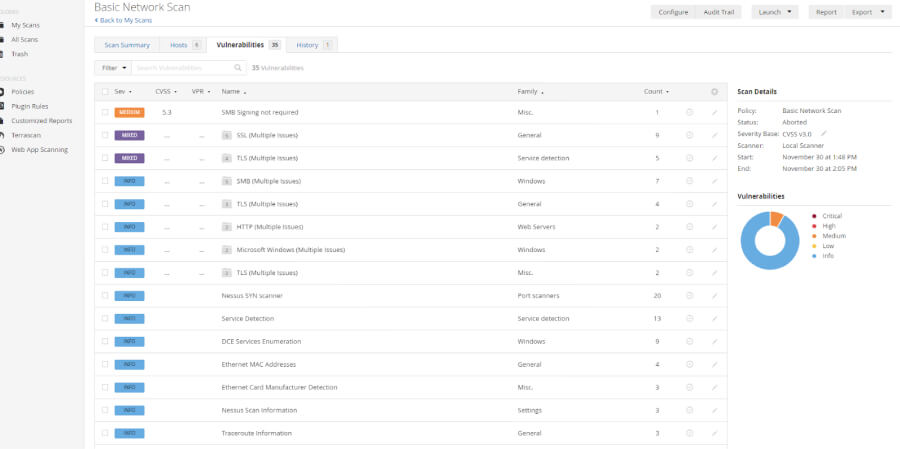
Tool 6: Nessus
Nessus is a widely used vulnerability scanner that performs comprehensive scans to help organisations maintain compliance with security standards. It's a powerful tool for identifying security weaknesses in networks and systems.
Pros:
- Comprehensive Scans: Able to detect a wide range of vulnerabilities, from common to rare.
- User-Friendly Interface: Offers an intuitive interface that simplifies the scanning process.
- Regular Updates: Keeps up-to-date with the latest threats and vulnerabilities, ensuring accurate results.
Cons:
- Costly: While a free version is available, the full features require a paid subscription, which can be expensive for some organisations.
- Resource Intensive: Running scans on large networks can consume a lot of system resources and time.

Tool 7: Cain & Abel
Cain & Abel is a password recovery tool that also functions as a network sniffer. It's used for cracking encrypted passwords and network keys, making it a valuable resource for ethical hackers.
Pros:
- Dual Functionality: Can recover passwords and sniff network traffic, offering versatility.
- Effective Password Cracking: Known for its effectiveness in decrypting passwords, especially weaker ones.
- Free to Use: Available for free, making it accessible to a wide range of users.
Cons:
- Complex Setup: Setting up and using Cain & Abel can be complicated, especially for beginners.
- Potential for Misuse: Due to its password-cracking capabilities, it can be misused for unethical purposes.

Tool 8: Kismet
Kismet is a wireless network detector, sniffer, and intrusion detection system (IDS). It captures Wi-Fi packets and detects network intrusions, making it an invaluable tool for network security.
Pros:
- Comprehensive Wireless Detection: Can detect various Wi-Fi signals and analyse network traffic effectively.
- Open Source: Available for free and supported by a community of developers, ensuring continuous improvement.
- Cross-Platform Compatibility: Works on multiple operating systems, including Linux, Windows, and macOS.
Cons:
- Complex Configuration: Setting up Kismet for specific network environments can be challenging.
- Limited IDS Functionality: While it can detect intrusions, it may not offer the same level of intrusion prevention as dedicated IDS systems.
Start Your Ethical Hacking Career with Online Courses Australia
Immerse yourself in the world of cybersecurity with our online courses tailored for aspiring ethical hackers. Whether you're looking to safeguard your own tech assets or aim to craft defence strategies for others, our course covers all you need to excel.
From the basics of ethical hacking and penetration testing to advanced network security techniques, our curriculum is designed to equip you with the skills necessary to thrive in this dynamic field.
What You'll Learn:
- Virtual Lab Environment: Engage in hands-on training in a simulated cybersecurity environment, perfecting your skills in real-world scenarios.
- EVM and INFOSEC Training: Prepare for key industry certifications like the Offensive Security Certified Professional (OSCP).
- Capture The Flag (CTF) Challenges: Test your skills with practical challenges, including exploiting SQL Injection to gain shell access.
Don’t just learn about cybersecurity—master it and become a defender of digital landscapes. Enrol now and take the first step towards becoming an ethical hacking expert in Australia.
Hacking Software FAQs
What are the 5 faces of hacking?
The "five faces" of hacking refer to different types of hackers based on their intentions and actions. These are commonly categorised as:
- White Hat: Ethical hackers who help organisations to improve their security.
- Black Hat: Malicious hackers who exploit vulnerabilities for personal or financial gain.
- Grey Hat: Hackers who may violate ethical standards or laws but don't have malicious intent like black hats.
- Blue Hat: Professional security professionals invited by companies to find vulnerabilities before a product launch.
- Red Hat: Hackers who actively seek to find and disable black hat hackers
What do ethical hackers need to know?
Ethical hackers should have a set of skills that include:
- Programming and Scripting: Understanding of programming languages like Python, JavaScript, and SQL.
- Networking: Knowledge of network structures, protocols, and both the theoretical and practical aspects of networking.
- Operating Systems: Familiarity with different operating systems, especially Linux, as many tools used for hacking are developed for it.
- Security Concepts: A strong grasp of security principles, risk assessments, vulnerabilities, exploitation techniques, and countermeasures.
- Legal Knowledge: Awareness of legal constraints around hacking activities to ensure they stay within ethical and legal boundaries.
What are the 6 phases of ethical hacking?
Ethical hacking can be divided into six phases to ensure thorough security testing:
- Reconnaissance: Gathering preliminary data or intelligence on the target.
- Scanning: Using technical tools to gather further intelligence on how the system is set up and behaves.
- Gaining Access: Using exploits to enter a system or network.
- Maintaining Access: Securing their presence in the system discreetly to gather as much information as possible.
- Covering Tracks: Erasing evidence of the hack to avoid detection.
Reporting: Documenting the findings and methods used to inform the client of security weaknesses and potential improvements.
Read more:
- Career Development





















